MITRE ATT&CK & The Cyber Kill Chain
Threat Hunting & Investigation
Malware Analysis
DFIR
Jan 1, 2026

In this blog post, we will discuss the MITRE ATT&CK knowledge base and how it can be used to make you a better digital forensic investigator, incident responder, or threat hunter. We will also discuss a very similar concept called the Cyber Kill Chain. By the end of this blog, you will come away with an understanding of how to use these two frameworks to think like a threat actor and perform more focused DFIR analysis.
What is MITRE ATT&CK?
MITRE is a not-for-profit organization which primarily serves United States federal agencies solving highly complex and technical challenges in service of the public-interest. ATT&CK stands for Adversarial Tactics, Techniques, and Common Knowledge. It started as an internal MITRE project in 2013, documenting cybersecurity threats against Windows enterprise networks.
Now, ATT&CK is a free globally accessible knowledge base available to any person, business, or organization. The knowledge base serves as a central repository for all adversarial tactics, techniques, and procedures (TTPs). In other words, ATT&CK has information on nearly every strategy ever used by threat actors. ATT&CK is used to detect, prevent, and fight cybersecurity threats by almost all professionals in the industry. As such, learning how you can use this knowledge base will level-up your DFIR skills and help you fight the cyber challenges ahead! Their website can be accessed here: https://attack.mitre.org/. Below shows how ATT&CK organizes information, let's explore the way this information is categorized.
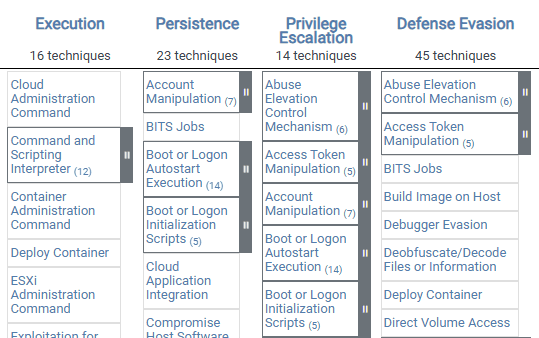
TTPs:
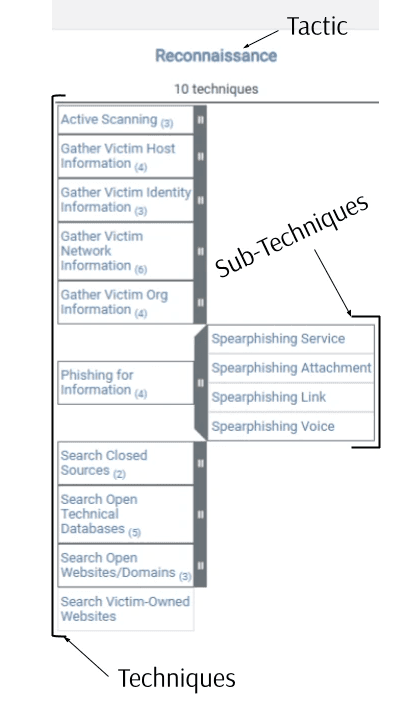
MITRE stores their adversarial information in the form of Tactics, Techniques, and Procedures. What do these terms mean?
1) Tactics: Tactics are adversarial goals. In other words, it is the reason for performing an action.
2) Techniques: A technique is the strategy or methodology used by the threat actor to achieve their goal, or tactic.
3) Sub-Techniques:A specific methodology which describes behavior at a lower-level than techniques.
4) Procedures: Procedures are specific implementations of techniques. The information kept here contains real-world examples of the technique including valuable details on the incidents.
Example:
Let’s use an example to explore these definitions. In the image above, we are examining the tactic known as reconnaissance. Reconnaissance involves an adversary gathering information about the target(s) for use in future operations. Therefore, reconnaissance, or gathering information, is the adversary’s Tactic. Next, the strategy the adversary uses to gather information will be their Technique. For our example, let’s assume the adversary is using the technique known as Phishing for Information. This is a broad strategy with many different ways the adversary could phish for information. The specific approach used by the adversary is the Sub-Technique. For our example, we can see that ATT&CK has four listed sub-techniques for Phishing for Information. Depending on the technique, there may be more, less, or no sub-techniques. For our example, let’s use the Spearphishing Link sub-technique. One procedure stored by ATT&CK details Dragonfly’s use of PDF attachments with malicious links to credential harvesting websites. Procedures are listed here: https://attack.mitre.org/techniques/T1598/003/
Matrices:
Currently, there are three different versions of MITRE ATT&CK, known as Matrices: Enterprise, Mobile, and ICS. Let’s review these to understand their differences and use cases.
Enterprise: The Enterprise Matrix is a knowledge base of adversarial TTPs specifically in regards to enterprise environments. Currently, the platforms with documentation are as follows: Windows, macOS, Linux, PRE, Cloud (Office Suite, Identity Provider, SaaS, IaaS), Network Devices (such as routers, switches, and load balancers), Containers, ESXi.
Mobile: The Mobile Matrix is a knowledge base of adversarial TTPs specifically in regards to Mobile devices. The knowledge base includes device access and network-based attacks. Currently, the supported platforms are iOS and Android.
ICS: The ICS Matrix is a knowledge base of adversarial TTPs specifically in regards to Industrial Control Systems. ICS are systems which control industrial processes, such as critical infrastructure like power grids, water systems, and manufacturing plants. ICS cybersecurity is growing rapidly. As more industries implement technological systems to boost efficiency, more adversaries try to exploit these systems!
Navigator:
ATT&CK Navigator is a free web-based tool that provides an interactive visualization of the ATT&CK matrices. This tool allows you to create custom layers highlighting specific techniques, track adversary behaviors, or document your organization's detection coverage. By color-coding techniques based on your criteria, the Navigator helps you quickly identify gaps in your defenses or focus your investigation on the most relevant TTPs. You can access the Navigator at https://mitre-attack.github.io/attack-navigator/ or download it for offline use.
Technique IDs:
Every technique and sub-technique in ATT&CK is assigned a unique identifier for standardized communication across the cybersecurity community. These IDs follow the format T#### for techniques and T####.### for sub-techniques. Using these IDs in your reports, SIEM rules, and team communications ensures everyone is referencing the same specific behavior, regardless of how they might describe it in words. When documenting your investigations or building detection rules, always include the relevant technique IDs to maintain clarity and enable others to quickly reference the full details on the ATT&CK website.
Applications:
The ATT&CK frameworks have many applications to a DFIR professional and other related fields. Now that we have reviewed ATT&CK and we understand how it stores information, let’s examine these use cases so you can learn how ATT&CK can benefit you.
1) Digital Forensic Investigations & Incident Response:
When conducting investigations, “going in blind” is not a good strategy. Investigators do not start to read log files or web history at random. There is a plan executed based on the available information. For example, when investigating a compromised network, there must be a point of initial compromise. By referencing the Techniques stored in the Initial Compromise Tactic, the investigator can search for specific strategies often employed by adversaries. Using this strategy is especially critical in incident response, as time is of great importance. Using the ATT&CK framework to guide your actions will ensure the process is focused, purposeful, and based on known adversarial behaviors.
2) Threat Hunting:
Threat hunting is the proactive security practice which mirrors the reactive DFIR practice. Instead of responding to the threat, threat hunters search for adversaries which have gone undetected in a given environment. As such, the ATT&CK framework is a critical guide to follow to hunt for threats. As these are undetected adversaries, the information available is almost non-existent and “going in blind” could take years to find anything! For example, by referencing the Persistence Tactic, a threat hunter can decide they should check the Windows Service sub-technique of the Create or Modify System Process technique.
3) Adversary Simulations:
Adversary simulations benefit tremendously from the introduction of ATT&CK. After all, this activity is designed to recreate the adversarial activities for a variety of goals. For anyone conducting adversary simulations, ATT&CK should be an often referenced guide to design plans. The framework can take the realism of the simulations to their peak, as attacks can be based on real life documented incidents.
4) Penetration Testing:
In penetration testing, you must not only think like an adversary, but act like one too! For this role, ATT&CK will provide you with proven methodologies which have been implemented by real adversaries in real world incidents. Utilizing ATT&CK to test the client's cybersecurity will ensure the client is getting the most informed and applicable recommendations possible. You can base your attacks on the real world incidents documented in the ATT&CK framework.
Cyber Kill Chain:
Now that we understand ATT&CK and its many benefits, let’s briefly discuss a similar concept which will serve as an addition to ATT&CK, the Cyber Kill Chain.
The Cyber Kill Chain is another cybersecurity framework which was developed by Lockheed Martin. It is much more of a framework, rather than a knowledge base, as it includes seven sequential steps which represent the stages of a typical cyberattack. The Cyber Kill Chain does not include a plethora of documentation regarding specific attack methodologies like ATT&CK. Instead, the seven step framework serves to represent the typical sequential flow of a cyberattack. So, the Cyber Kill Chain will not provide details of common techniques, but it should still be known to all DFIR professionals to get a better understanding of adversarial behaviors.
Let’s briefly explore the seven steps of the Cyber Kill Chain. Refer to the graphic below to learn about each of the seven steps.
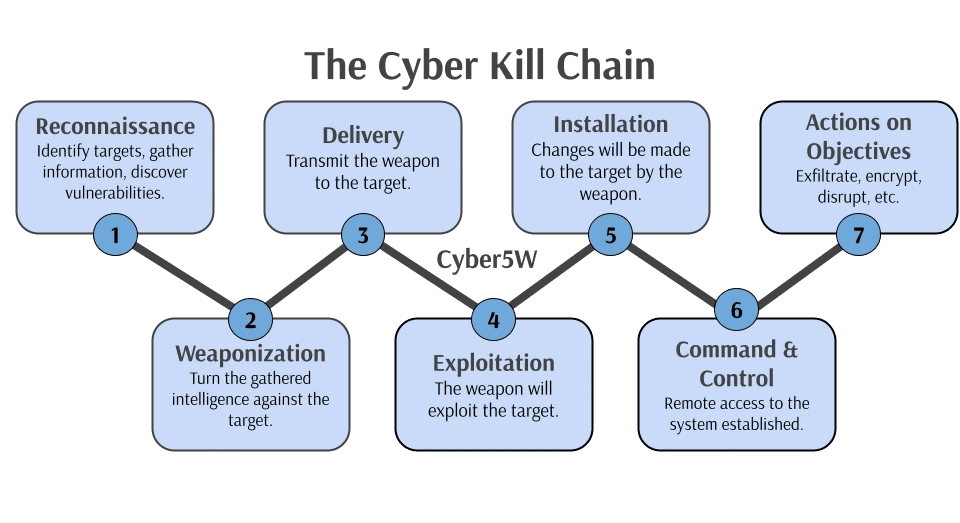
Reconnaissance: During this first step, adversaries will attempt to gather information, including identifying the specific target and discovering vulnerabilities to be exploited. This can be done passively, without the adversary ever interacting with their target(s), although this does not yield the best information. It can also be done actively, with the adversary interacting with the target and therefore leaving behind evidence of their interactions. One example of this could be an adversary using nmap to perform a port scan against a target to identify their open ports and running services. Another example could be an adversary using a tool like sqlmap to probe a web application for an SQL injection vulnerability. Using these examples, it’s clear that active reconnaissance leaves behind digital evidence to be investigated. Early detection during this step of the Cyber Kill Chain could stop an adversary before they gain access to a system.
Weaponization: In the second step, adversaries attempt to turn the gathered information against the target. One of the most common examples is the use of known exploits. Unskilled adversaries may discover a vulnerability which has already been exploited by someone else. Therefore, they can use a website like exploitdb to find the exploit they need. For more advanced adversaries, this step may include the creation of a new exploit script or malicious program. In some examples, an exploit in the form of malicious code is not needed. Sometimes, the discovered vulnerability could be company emails and the weaponization could be carefully crafted phishing email. Regardless, after having gathered information, adversaries need to turn this intelligence against the target.
Delivery: The third step involves the adversaries delivering the weapon to the target. This step is closely related to the previous, as often during the weaponization of information, the adversaries will establish how they will deliver the weapon. Based on the weapon, this could come in many forms. As previously discussed, the discovery of an open port could allow direct file transfer, the discovery of a vulnerable web application could provide access to the host system, or accessing leaked company emails may result in creating an email account impersonating a third-party vendor for delivery through a phishing email.
Exploitation: In the fourth step, the weapon created and delivered using the gathered intelligence will exploit the target. As seen in our three examples, this can come in a variety of methods. Most notably, there is likely to be significant evidence created during this step. Furthermore, this can often be the first step where incident responders become aware of a cyber incident.
Installation: The fifth step involves additional changes made to the target by the adversary. After the exploitation, the adversary will attempt to create persistence mechanisms, elevate privileges, or move laterally in the network. These actions will create many changes to the system or network and lead the adversary closer to their ultimate goal.
Command & Control: The sixth step involves solidifying remote connection to the system or network. Based on the changes observed in the previous phase, this could be achieved through a variety of methods. For example, a new user account could be created with RDP privileges. This change solidifies remote connection to the system.
Actions on Objectives: The final step encompasses the adversary achieving or attempting their actual objective. With solidified remote access to the system, the adversary can start to achieve their end goal. Some common examples could be data exfiltration, disrupting services, or trade secret theft.
Understanding all seven of these critical steps in a typical cyberattack is critical to all DFIR professionals. During an investigation, consider this sequential pattern as a guide as to where to look or what to expect next. Furthermore, when responding to a live incident, consider at what step the adversary may be in the Cyber Kill Chain and how to best respond to their current phase of the attack pattern.
Although it should be noted that not all cyberattacks follow the 7 steps of the Cyber Kill Chain. The Cyber Kill Chain is one framework of many which can be used to understand adversarial behavior, it is not the definitive adversarial playbook. One of the main shortcomings of the Cyber Kill Chain is that it is linear, depicting cyberattacks neatly flowing from one step to the next.
Another adversarial framework called the Diamond Model, which was created in 2013 by the U.S. Department of Defense, is a multidimensional model designed to help establish the basic elements of any intrusion activity. This can also be a powerful framework, which when combined with the Cyber Kill Chain, grants a deeper understanding of a cyber incident. A full examination of the Diamond Model is out of this blog’s scope, but if you’d like to read the report it can be found here:
https://apps.dtic.mil/sti/pdfs/ADA586960.pdf
Conclusion:
MITRE ATT&CK and the Cyber Kill Chain are two critical frameworks for modern DFIR professionals. ATT&CK provides the granular, technical details of adversarial behaviors across enterprise, mobile, and ICS environments, while the Cyber Kill Chain offers a high-level linear view of a typical cyberattacks progression.
No matter your role in the world of cybersecurity, these two frameworks, and others like them, will help you in your daily work. Now that you have a baseline understanding of these two frameworks, I encourage you to continue reading about ATT&CK and remember the steps outlined in the Cyber Kill Chain when investigating an incident.
It’s important to note, ATT&CK is a living document which is consistently updated. Remember to stay up to date on the latest TTPs released by MITRE. Additionally, keep in mind that other frameworks exist, which can add new layers to your understanding of cyberattacks and will certainly help you in the world of cybersecurity.
Authored by:
Mitchell Biagini
Frequently asked questions
Still have questions?
Can’t find the answer you’re looking for? Please chat with our friendly team.
